Continuous Automated Red Teaming: From One-Off Tests to Persistent, Realistic Security
Cyberattacks are non-stop, so why are your security tests only once a year? Traditional red teaming is a static snapshot that leaves you exposed. This article introduces Continuous Automated Red Teaming (CART), a revolutionary approach that uses AI and MITRE ATT&CK mapping to provide persistent, realistic defense validation 24/7. Understand how CART closes security gaps, accelerates Blue Team readiness, and transforms your security posture from reactive to proactively resilient.
Kerlyn Manyi
10/29/20254 min read


Cyber threats evolve at a blistering pace. One week, it’s a zero-day exploit of a popular VPN appliance; the next, a sophisticated phishing campaign built with generative AI. Attackers constantly shift tactics, searching for the slightest crack in an organization’s defenses.
Traditional red-team exercises help expose those weaknesses, but they usually happen only once or twice a year. That schedule is no match for adversaries who adapt in real time. By the time a test wraps up, attackers may have already discovered new vulnerabilities, leaving organizations unknowingly exposed.
Continuous Automated Red Teaming (CART) closes that gap. It delivers persistent, AI-powered testing that runs around the clock, constantly probing defenses the same way real attackers do. CART turns red teaming into an always-on safeguard, helping organizations strengthen security before cyber threats strike.
Why Traditional Red Teaming Falls Short
Traditional red team exercises are essential for exposing weaknesses, yet they are static snapshots in a constantly shifting battlefield. That means:
● Gaps between tests allow new vulnerabilities to go undetected.
● Limited scale: Skilled red teamers can only cover so much ground.
● Static tactics: Repeated test scripts miss evolving adversary techniques.
The result? Defenses that decay over time and blind spots that attackers can exploit.
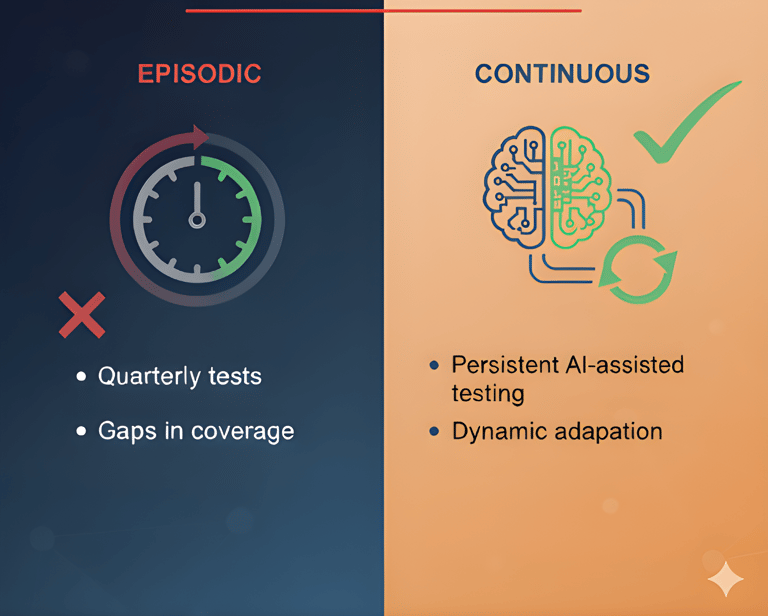
Continuous Red Teaming: A Smarter Approach
Continuous Automated Red Teaming (CART) extends traditional red teaming into a persistent, intelligent operation. Instead of one-off campaigns, it continuously probes, tests, and adapts to your environment, running 24/7.
CART enhances efficiency by:
● Reducing human error through AI-driven automation.
● Scaling red team coverage across large infrastructures.
● Providing real-time feedback for immediate mitigation.
Whether you’re a security practitioner trying to outpace attackers or a business leader protecting critical data, CART changes the game - moving from reactive assessments to proactive defense validation.
The AI Engine Behind CART
AI powers CART’s ability to simulate complex, evolving attack behaviors:
● Imitation learning helps the AI model replicate how expert red teamers think and act.
● Reinforcement learning allows the system to adapt its tactics as defenders respond.
● Behavioral analytics identify subtle weaknesses, even as environments shift.
Together, these capabilities enable AI to continuously explore attack paths, learn from defender responses, and uncover gaps before adversaries do.
MITRE ATT&CK Integration
Every simulated attack can be mapped to MITRE ATT&CK techniques, giving defenders a clear picture of how an attacker might move through the network.
For example:
● T1078 – Valid Accounts: Detect how the AI exploits weak credentials.
● T1021 – Remote Services: Observe simulated privilege escalation.
● T1041 – Exfiltration Over C2 Channel: Identify when data could leave the network.
Mapping these simulated attacks to ATT&CK gives defenders a structured, transparent way to assess and improve coverage across all threat phases. This ensures AI tests are realistic, standardized, and actionable.
A sample workflow will look thus;
Human experts define objectives and attacker goals
AI imitation learning models human decision-making
Reinforcement learning adapts tactics to defender responses
Actions mapped to MITRE ATT&CK for analysis
Analysts review results and improve defenses
Building Collaboration: CART Meets Blue Team Operations
Not every red team engagement involves the defenders but when it does, the results are transformative. Integrating your blue team (defensive analysts, SOC operators, and incident responders) into CART creates a closed-loop ecosystem where attacks and defenses evolve together.
This collaboration means:
● Blue teams improve their detection and response tuning based on realistic attack data.
● Red teams gain better insights into defensive blind spots and response times.
● Organizations build a continuous learn-and-adapt feedback cycle that strengthens their overall resilience.
Why Continuous Red Teaming Matters
Continuous, AI-driven red teaming provides advantages that traditional methods simply can’t match:
● Persistent validation: Identify weaknesses as they emerge.
● Defensive readiness: Measure how well your blue team responds in real time.
● Proactive resilience: Mitigate risks before attackers exploit them.
● Consistent benchmarking: Use ATT&CK mappings to track improvement over time.
● Actionable insights: ATT&CK mapping ensures every finding links to real attacker behavior.
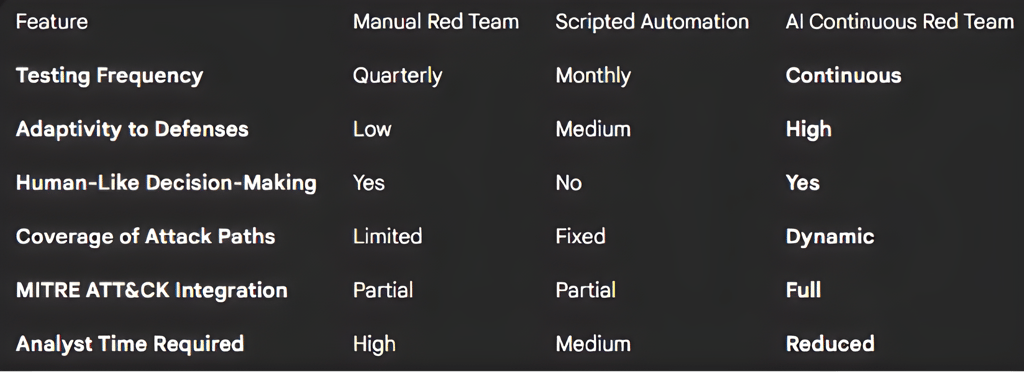
Comparison Between Manual Red Teaming, Scripted Automation, and AI-Driven Continuous Red Team Exercises
Challenges and Considerations
Several platforms today already bring aspects of continuous security validation to life. They allow teams to automate attack simulations, benchmark defenses, and integrate results into MITRE ATT&CK frameworks.
While CART introduces speed and scalability, it’s not without challenges:
● False positives from imperfect baselines.
● Lack of true adversarial reasoning in current tools.
● Model drift as environments evolve.
● Continued need for human oversight.
CART should be implemented in controlled environments (such as cyber ranges) to ensure safe, measurable, and compliant operations.
The Future of Continuous Red Teaming
The future of Continuous Red Teaming will merge existing automation frameworks, fix the limitations to make it human-centric with adaptive AI systems capable of:
● Learning and mimicking attacker behaviors through imitation learning.
● Continuously refining attack strategies via reinforcement learning.
● Mapping and prioritizing impact across MITRE ATT&CK techniques in real time.
● Safely simulating adversarial behavior within controlled cyber ranges.
● Creating a human-in-the-loop governance model where analysts oversee, tune, and learn from AI-driven insights.
This is the shift from automation to autonomy, where red teams don’t just run preloaded scenarios, but continuously reason, adapt, and evolve like real adversaries.
The organizations that embrace this next generation of CART, grounded in AI, ATT&CK mapping, and human collaboration, will build a defense posture that learns as fast as the threats it faces.
“Attackers innovate daily — your defenses should, too. Continuous Red Teaming ensures you’re not just reacting but staying one move ahead.”
